Examining the Meraki Fullstack (Part 5)
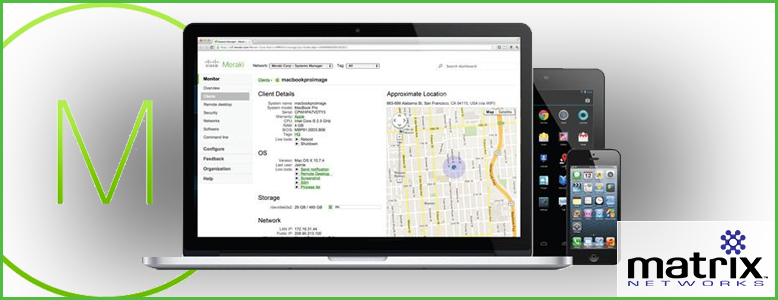
The Meraki Systems Manager is a MDM (Mobile Device Management) platform that allows for a central dashboard showing all device information, with the ability to apply policy, deploy, remove, and update software on all devices across your network with a few clicks.
The platform has adopted a wide range of devices including Apple, Android, Mac and PC. Systems Manager utilizes an agent deployed on any device that you wish to manage and monitor. There are many avenues to enroll devices including using a dedicated Meraki wireless network and scanning QR codes. Those companies that have chosen Apple mobile devices can have them shipped with the MDM platform already deployed and pre-configured making roll-out to remote users a cinch. Once the agent is deployed device information starts pouring into the dashboard.
Devices on the dashboard provide a wealth of information that is traditionally very difficult to collect such as hostname, model, serial number, disk utilization, installed software, MAC addresses, operating system and version, location, and much more. With Meraki SM, all this information and more is available with a few clicks. Many companies have no handle on any of this, and at best have an outdated spreadsheet of this information. Having this level of information improves the speed of issue resolution, reduces frustrations of employees (especially remote ones) and simplifies replacement cycles.
Security Risk Associated with Mobile Devices
Remote devices can be a security risk and the SM platform includes features to set security policy and report on compliance of those policies. Depending on the platform you can choose to disable cameras, disable screenshots, enforce complex passwords and pins, limit the device to only joining certain wireless networks, and that is really the tip of the iceberg. On desktops, these range from requiring a firewall and antivirus to be running, to requiring a device to be at a certain OS or patch level. The security policy is also designed to give you the ability to run with whitelisted only applications, or blacklist certain applications. If devices are intended to remain in a certain place SM Geofence function alerts when devices leave the designated area. This can be incredibly helpful for organizations using devices like retail point of sale, or tablets in a dental office. If devices do walk away or are stolen the devices can be remotely wiped in seconds.
Application Management
Managing and pushing applications is also a key component of the SM platform. Applications can be pushed to devices and even be forced to be up-to-date. For phones and tablets the respective application stores (App Store and Play Store) can be searched for specific apps and pushed down to your devices, for Windows devices an executable or “msi” file can to used. Applications can be marked as mandatory, and alerts can be generated if a device doesn’t have a mandatory application on it. Beyond the ability to push application, all applications across all devices are inventoried. This provides administrators a central place to search and see what application are on which devices, and the respective versions of those applications. This information can be powerful when auditing for software licensing, usage and version mismatches.
So far, we have covered the highlights for the MDM platform in a standalone fashion. Like all things in the Meraki Stack, the more you combine the more powerful the total solution becomes. The MX Security appliances and MR Wireless Access Points are aware of devices that have the Systems Manager installed and allows for all kinds of interesting integrations. To highlight these let’s look at a common issue for most business: BYOD devices. In most environments, there are company issued devices, but most users have a phone in their pocket that they want to connect to the Wi-Fi. There generally isn’t a great way to keep the users off the main company SSID, allowing unsecured devices onto the network. With the MR Access Points you can force clients to have the Systems Manager client installed to join the network. Once the Systems Manager is deployed on corporate and BYOD devices, different policies can be applied to them in a dynamic way. On a single SSID you can apply different L3 and L7 firewall rules, change what VLAN the device traffic is egressed onto, and set different bandwidth and traffic shaping rules. At the security appliance, you can apply similar policies in addition to AMP/IPS and content filtering for different devices types. Now opposed to the legacy way of having multiple SSIDs, or worse yet not having multiple SSIDs, you can seamlessly have a single wireless network all clients associate to that dynamically applies policy, reducing complexity the Meraki way.
Why Matrix Networks Partners with Meraki?
Although Meraki products come at a premium, we have discovered the value of the analytics, performance, troubleshooting tools, and ease of use. All of which make Meraki an excellent value, especially when paired with the full-stack for complete network control. To learn more about Meraki’s platform you can schedule a demo with our team, watch a webinar (and receive a free AP), and even try it yourself on a trial. As a Premier Cisco Partner, Matrix Networks is here to assist in anyway we can. Let us know how we can help.
The combination of smart management with the most powerful network toolset in the world gives Meraki a significant edge that all the other major players are chasing. In this article we will expand on why Meraki is winning the battle for network infrastructure.
Author: Kyle Holmes


.svg%20(1).png?width=55&name=1200px-Logo_of_YouTube_(2015-2017).svg%20(1).png)

